When word broke several weeks ago that Target had been hacked and many of their customer’s personal information had been compromised, it raised concerns by consumers and many in the public concerned with how their information is being collected and stored.
The company is working to clean up its image from the incident and handling with the fallout, which will cost it more than $500 million. While it’s impossible to completely protect sensitive information from hackers, security professionals say there are steps public and private entities can take to make it much harder for such incidents to occur.
“We’re not signaling out Target and saying they did anything wrong,” said Ken Hosac, vice president of business development for CradlePoint during a Feb. 25 webinar. “We’re using them as a way to illustrate the issues because basically the situation they have gone through, this Target breach is the Hurricane Katrina of retail networking.”
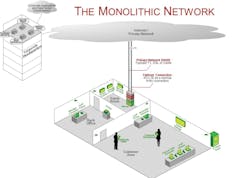
One of the big issues entities have in securing such information is the use of a monolithic network that allows for hackers to get to sensitive data by accessing a different point on the network. Hosac said oftentimes hackers will gain access using phishing and spear phishing techniques to get someone within the company to open an email link or attachment so they get access to the system.
Hosac said hackers then find different weak spots within the network to access other areas until they eventually reach a spot to enter the area with sensitive data.
“This was a very sophisticated attack,” said Kent Woodruff, chief security officer for CradlePoint. “But the tools used to do it are very readily available.”
While phishing involves sending out emails in a “shotgun” fashion to get someone within the company to open an link or file, Hosac said spear phishing is sent out in a very targeted way using emails that look legitimate and that could pertain to information within the company. Company information can be accessed from different company files kept on a particular server that are shared with other employees because the often contain passwords or email information.
“Company executives, a lot of them don’t understand they’re an easy, easy target for a lot of this,” he said.
In order to combat such a situation, Hosac said entities should considered putting in parallel networks within their buildings or organizations in order to keep different areas from connecting. Some companies will have one router that only deals with payment information while employee human resources access will be on another network and security cameras will be on yet a different network.
Entities will also keep public Wi-Fi on a different network and if there are third party vendors within an area, such as a vending machine at a train station, it will be on its own network.
Hosac said buses are an interesting case because they have digital signage on the outside, fare collection equipment collecting customer financial data, Wi-Fi, more digital signage on the inside, at least three security cameras and route trackers for riders to follow. It’s not feasible to have a separate router for each different part of the bus, so Hosac said segmentation would be a better choice in keeping information safe onboard.
“What’s key is they’re not using it to store any credit card data on the machine,” he said. “It all goes straight up to the cloud as opposed to being able to accessing any local data on that bus.”
Costs associated with the new networks can also be mitigated by carefully selecting the right network provider.
Going with DSL or cable will cost roughly $50-$60 per month and T1 access costs anywhere for $300 on the low end to $1,000, said Woodruff. Some may opt for 4G access, which can be less than $10, but it’s important to understand how much data is being used because costs will go up after the allotted monthly allowance is used up.
He said there are very few areas where customer access to 3G or a 4G network will be impaired due to congestion, but oftentimes multiple modems will be set up for redundancy and access at least two providers in order to handle performance issues or handle outages.